Faster Threat Detection and Response
Authored by Ericsson
Distributed denial of service (DDoS) flooding attacks are one of the most effective methods to destroy the availability of critical IT infrastructures and, therefore, one of the main threats that infrastructure and service providers still have to face [1].
These DDoS attacks cannot be prevented ahead of time, and once in place, they overwhelm the infrastructure with huge volume of traffic and render it not only incapable of performing normal communication but often completely out of control with no possibility to activate any countermeasure or mitigation action.
For example Yahoo!, who experienced one of the first major DDoS flooding attacks, saw their services offline for about 2h [2].
The same happened in occasion of the “largest ever” internet attack, when a 9 of the 13 domain name system (DNS) root servers were shut down for an hour-long DDoS flooding attack [3], or the notorious IoT device based DDoS attack that involved malicious DNS lookup requests from tens of millions of IP addresses that rendered major Internet platforms and services unavailable to large swaths of users in Europe and North America for several hours throughout the day [4].
Considering that any delay in detecting the flooding attacks risks to make any mitigation action useless, the challenge is to effectively provide a near-real time attack detection able, at the same time, to face the explosive increase in the volume of Internet traffic and evolving sophistication of the attacks.
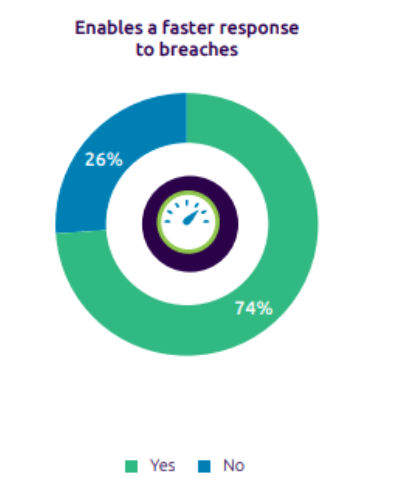
This is, therefore, also one of the main requirement and expectation coming from the market [5] as we can see in the picture (“Reinventing Cybersecurity with Artificial Intelligence”: nearly three in four executives among a representative sample of 850 ones, is expecting AI to provide an effective faster response to breaches), and this is clearly on of the main objectives of the HORSE project threat detector.
To optimize the detection and make it as fast as possible, we acted on different aspects of traditional detectors, operating in novel ways and in parallel from different perspectives which are implemented for the first time in this innovative framework, and which will be progressively illustrated using the dissemination channels of the project.
According to a top-down approach, beyond a complete architectural re-thinking “outside the box” and re-design of the classical machine learning threat detector solutions introducing new multi-stages structures that provided multiple important benefits from the detection time perspective, the study and testing activity has progressed to the level of the specific Machine Learning algorithms optimizations.
Following the simple illustrative diagram shown in the next figure, the Machine Learning usual strategies [6] (which have already proven to be significantly faster than the previous techniques) are able to identify alarm conditions by dynamically comparing the values monitored by the network with the expected values, which are predicted based on a model initially obtained from the preliminary learning phase and then continuously dynamically updated.
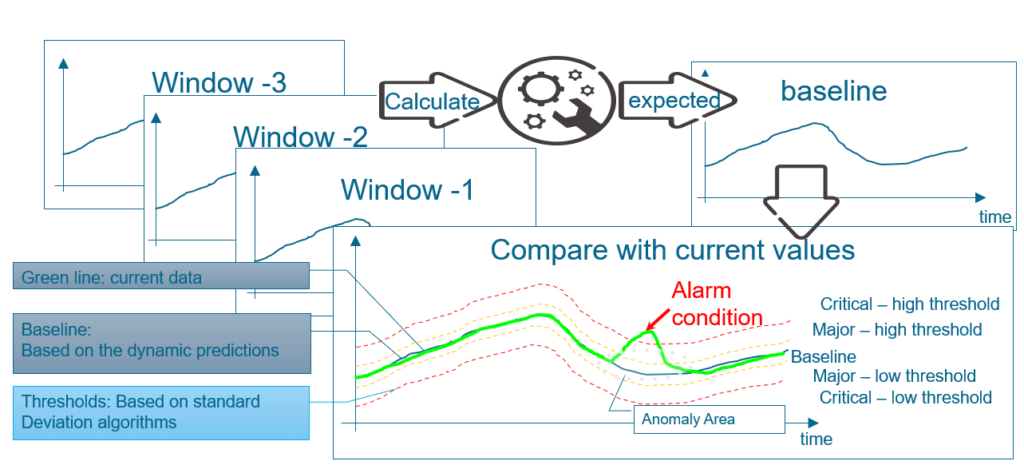
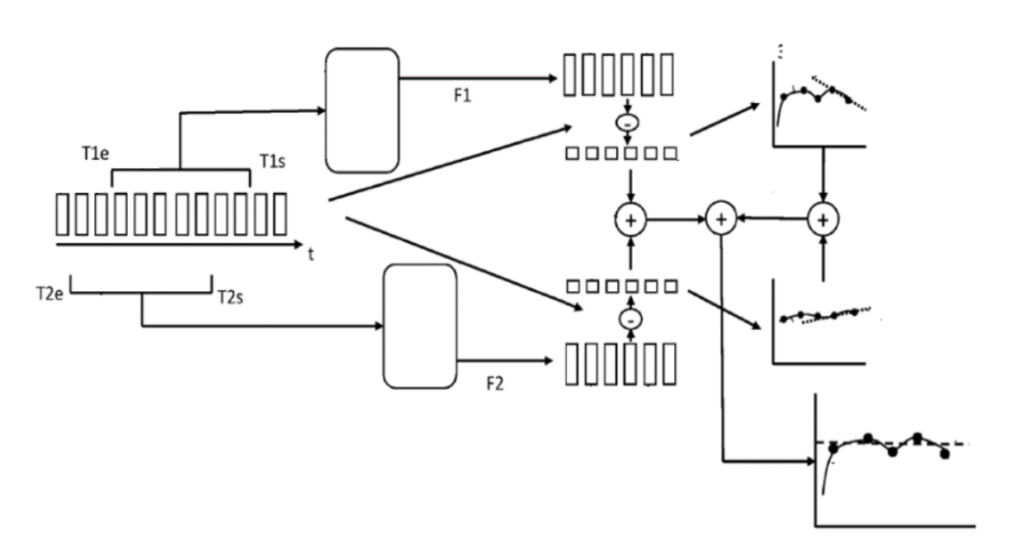
Precisely the process of dynamic updating of the model, which is undoubtedly a strength point as it automatically allows the forecasts to follow and adapt to evolutions in infrastructure, traffic, etc., constitutes, depending on the characteristics of the time series being analyzed at input, an important weight in the total detection time. Studying in detail the different impacts of various computations in the overall timing budget, it has been demonstrated that the replacement of standard Machine Learning regressions (e.g., Linear, ARIMA, SARIMA etc.) with a weighted linear combination of concurrent regressions working on the original time-series x(t), on its time-shifted versions x(t-nT), and on their derivatives (i.e., interpolations of their residuals, defining residuals the differences among the received and predicted values) is able to provide an important gain in terms of detection speed [7].
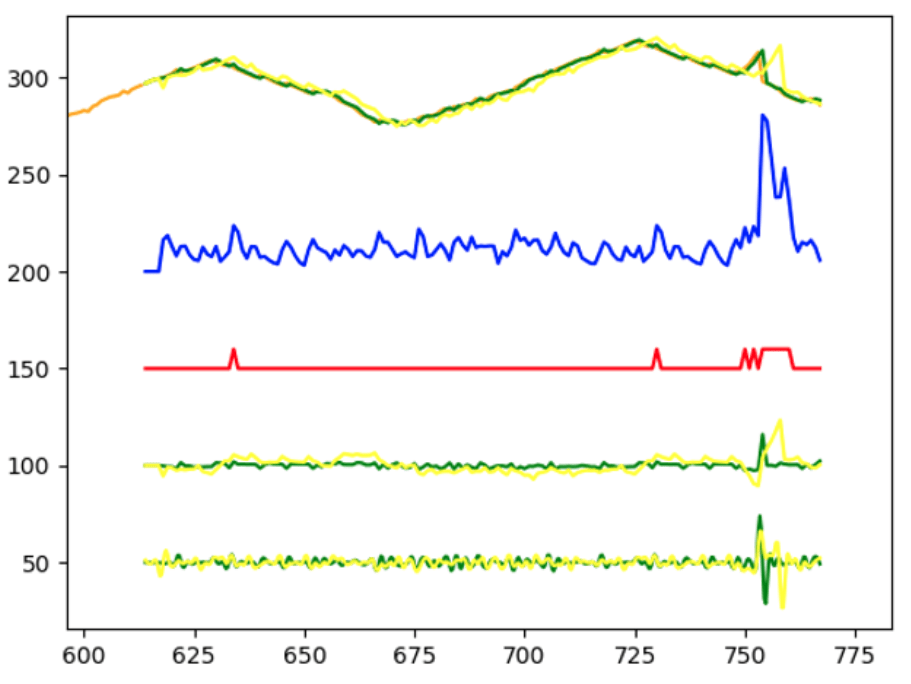
In this picture, from top to bottom, we can see:
- Real data (orange), ARIMA forecasts (green [original time-series] and yellow [time shifted time-series]
- ∆Tot Overall result of the overall linear combination (plus 200 to plot it)
- A warning-signal elaborated starting from ∆Tot (red) (plus 150 to plot it)
- Difference between regressions forecasts and real values (green and yellow) (plus 100 to plot it)
- Derivative functions of difference series (green and yellow) (plus 50 to plot it)
We can easily see the very low latency from the anomaly condition to the warning signal in comparison to a standard regression applications:
The HORSE project will carry out this type of investigation for the creation of an increasingly high-performance and high-speed threat detector to improve the security and resilience of critical infrastructures even in the face of new emerging and increasingly complex threats.
We are happy to communicate and disseminate our outcomes using all the available project channels, therefore you are kindly invited to visit the HORSE website and social media if you like to receive further information and details.
[1] HADEC: Hadoop-based live DDoS detection framework http://www.wired. com/. Accessed 09 July 2018 – file:///C:/Users/EORATOS/Downloads/HADEC_Hadoop-based_live_DDoS_detection_framework.pdf – https://www.researchgate.net/figure/Total-time-to-detect-DDoS-attack-in-HADEC-with-500-threshold-detection-time-is-measured_fig9_326724757
[2] Yahoo on trail of site hackers, wired.com, Feb. 8, 2000. http://www.wired. com/. Accessed 09 July 2018
[3] https://securityintelligence.com/articles/20-years-cybersecurity-largest-ever-ddos-attack/
[4] C Kolias, G Kambourakis, A Stavrou, J Voas, DDoA in the IoT: Mirai and other botnets. Computer. 50(7), 80–84 (2017)
[5] Reinventing Cybersecurity with Artificial Intelligence – The new frontier in digital security https://www.capgemini.com/gb-en/wp-content/uploads/sites/5/2022/05/AI-in-Cybersecurity_Report_20190710_V05.pdf
[6] Sketch-based Change Detection: Methods, Evaluation, and Applications – Balachander Krishnamurthy, Subhabrata Sen, Yin Zhang AT&T Labs–Research – Yan Chen University of California Berkeley, CA, USA
[7] Gemme Luciano, Cappelli Marco, Ericsson Patemte WO2021190760 “Determining an Alarm Condition” https://www.patentguru.com/search?q=WO2021190760
